Learn how an incoming one-way trust, sometimes used as "Active Directory Red Forest Design" or "Enhanced Security Administrative Environment" (ESAE), still constitute a security risk for the trusted domain/Red Forest if attackers have control of the trusting domain. This risk was reported to @Microsoft but will not be patched any time soon. Possible mitigations and detections are, as always, included in the post.
SID filter as security boundary between domains? (Part 6) - Schema change trust attack - from child to parent
In part 5 of this series, we explored how the replication of Configuration naming context (NC) allows for the GoldenGMSA trust attack. Exploring what else is stored in Configuration we find the AD Schema, and this post explores how this schema replication allows a child domain to modify the schema and thereby compromise objects in the parent domain, just as if you were a Schema Admin (a group only existing in the root/parent domain of AD).
SID filter as security boundary between domains? (Part 5) - Golden GMSA trust attack - from child to parent
In part 4 of this series, we saw how the replication of Configuration naming context (NC) to child domains allows for the GPO on site attack. Right after discovering this, the GoldenGMSA tool by Yuval Gordon was released, which makes it possible to compromise the password of a Group Managed Service Account’s (gMSA) in a domain if high privileges are obtained in the same domain.
Combining the Configuration NC replication attack research and the GoldenGMSA tool we found that another child to parent attack is possible.
SID filter as security boundary between domains? (Part 4) - Bypass SID filtering research
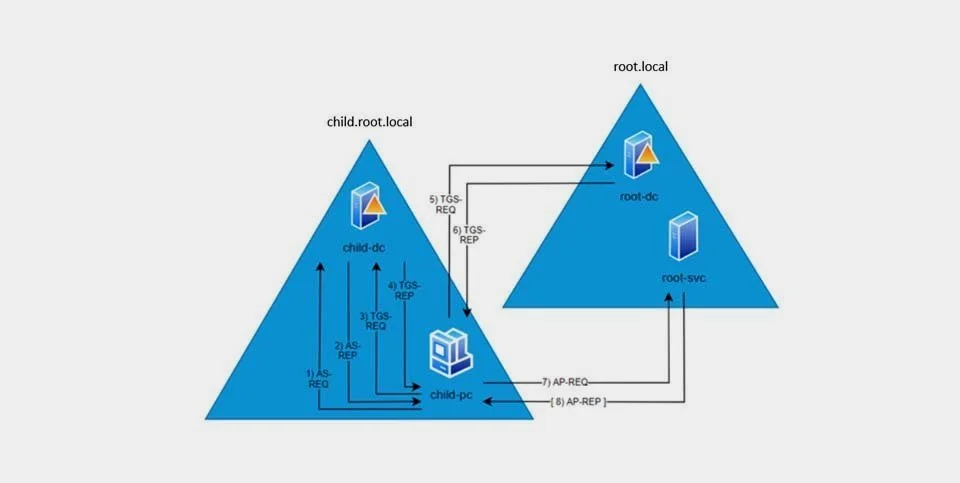
As demonstrated in part 3 (SID filtering explained), the Enterprise Domain Controllers SID, TDO SIDs, and NeverFilter SIDs were exempted from domain trust SID filtering. This blog post aims to identify rights granted to any exceptions, which can result in attacks from a child to a parent domain, thereby bypassing SID filtering as a security boundary. Two attacks, which we believe are novel, will be described: Keys container trust attack and DNS trust attack, for each we provide possible mitigations and detections, but as the conclusion says: we deem our suggested mitigations lowers the risk by such a small amount that the risk of mitigations breaking functionality is not justified. Additionally, we will describe an attack unrelated to the SID filtering exceptions: GPO on site attack.
SID filter as security boundary between domains? (Part 3) - SID filtering explained
This blog post is part three of a seven-part series.
This blog post will explain SID filtering for an intra-forest AD trust and demonstrate how SID filtering prevents the attacks shown in part 2: Known AD attacks – from child to parent. It’s not necessary to read part 2 first, but it is recommended.
Read2Own: Red Teaming Microsoft Azure
This blog post will showcase different techniques for obtaining access to Azure from the internet, escalating privileges within Azure, lateral movement between service principals, resources and users, persistence, and exploitation.
We've included a complete deployment guide including PowerShell scripts, so you can learn to abuse insecure Microsoft Azure configurations in your own tenant.
Furthermore, we've also included the detection and improving security section, which will allow you to re-configure your vulnerable tenant to a more secure design and detect if any of these attacks have been performed against your own tenant. Feel free to try the different attack paths in your own environment and see how you easily can disrupt the attack chain by hardening your tenant.
3 different sections will be covered:
Deployment
Attack Path (Overview and step-by-step)
Detection & Improving Security
SID filter as security boundary between domains? (Part 2) – Known AD attacks - from child to parent
This blogpost will demonstrate how an attacker with Domain Admin access in child domain can escalate to Enterprise Admins using known attacks. Various misconfigurations and vulnerabilities also make it possible to accomplish this escalation, the methods covered in this blogpost are all based on Kerberos weaknesses which work in a default AD environment and are rarely prevented.
SID filter as security boundary between domains? (Part 1) - Kerberos authentication explained
Can SID filtering create a security boundary between domains?
While researching this question, inspired by a comment on the Active Directory (AD) trust blogpost by harmj0y, which asked if enabling SID filtering on a child-parent trust (QuarantinedWithinForest) would prevent the SID history/ExtraSids attack from compromising the parent AD domain, @Martin, @Jonas, and @Tobias kept finding interesting new things.
What they expected to be a short blog post turned into a seven-part series, as they explored how to exploit Kerberos flaws to become Enterprise Admin, prevention against publicly known attacks, and finally, some novel bypasses to the prevention.
In part one of the series, they outline the underlying Kerberos authentication mechanisms to set the context for the attacks, defences, and research in the rest of the series. Read it here.
Privilege escalation vulnerability in Anaconda3 and Miniconda3
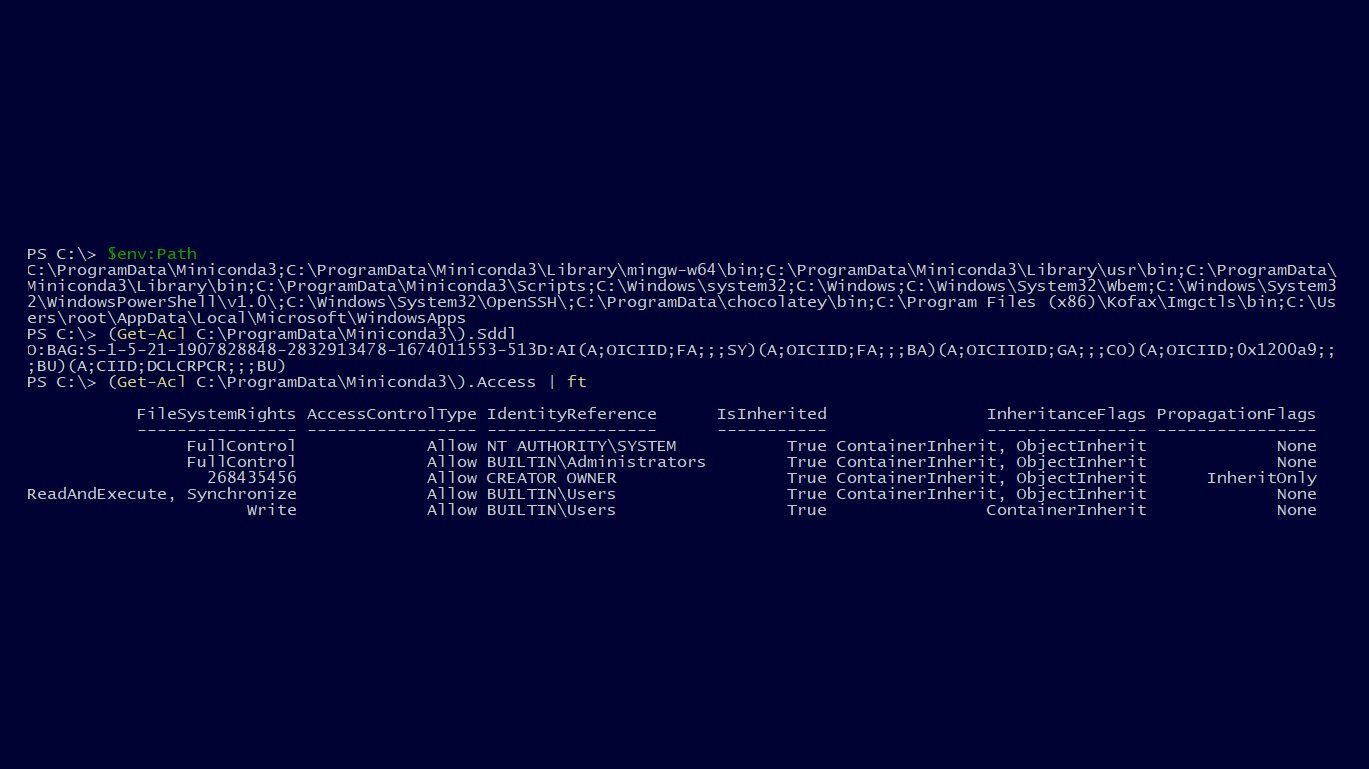
Responsible Disclosure! During a customer engagement, Security Advisor Martin Sohn Christensen discovered a privilege escalation vulnerability (CVE-2022-26526) in the Python data science package management applications Anaconda3 and Miniconda3.
As Martin describes it: “This is a classic PATH environment variable vulnerability present in non-default installation scenarios. We informed the vendor, however, three months after later no patch exist, we, therefore, follow our responsible disclosure policy and release it to the public.”.
Network share risks – deploying secure defaults and searching shares for sensitive information (credentials, PII, and more)
One of many low-hanging fruits I still see in our Active Directory Security Analysis and Internal Penetration Test is clear text credentials stored on domain-wide accessible network shares. These credentials are sometimes for service accounts and Domain Admins, meaning a threat actor with access to any user could compromise the entire Active Directory and its systems.
Staging Cobalt Strike with mTLS using Caddy
Multiple vulnerabilities in SonicWall SMA 100
What is the likelihood of recovering deleted iPhone messages?
Recent discussions regarding the SMS message retention policies of Danish Politicians sparked by a controversial decision by Prime Minister Mette Frederiksen to cull Denmark’s fur farm mink has led to an interest in the technical possibilities of recovering deleted iMessages from Apple iPhones.
Prime Minister Frederiksen had activated an iPhone feature where messages, SMS and iMessage, were deleted if they became older than 30 days. Can this iOS feature be hacked to recover messages?
Check and harden your Linux kernel security parameters with sysctl …and automatize it!
The command prompt has been disabled by your administrator. Press any key to continue... or use these weird tricks to bypass – admins will hate you!
The restriction is often seen in environments such as kiosks PCs and prevents an interactive command prompt with the goal of reducing the possibilities of an attacker.
This post explains how the restriction may be bypassed to obtain (interactive) command execution via Command Prompt to increase the possibilities in a penetration test. Mitigations against these bypasses can be found at the end of the post.
Think twice before launching into the skies – Hybrid identities and separation of workloads and infrastructure in Azure
Are you considering converting your corporate users into hybrid identities and taking advantage of the cloud technologies provided with Azure? Read how to configure your on-premises and cloud infrastructure a bit more securely while you transition some of your workloads and identities into the Azure- and Microsoft 365 cloud.
Read how to avoid hidden permissions and attack paths from on-premises to the cloud and learn ways to mitigate and detect misconfigurations by separating identities and privileges, while also configuring security boundaries in your Azure resource infrastructure.
Updates to Improsec Password Solutions
Privilege escalation vulnerability in NinjaRMM Agent MSI Installer introduced by EXEMSI MSI Wrapper
ImproHound - Identify AD tiering violations
It is extremely difficult to uncover the security implications of the many permissions configured in a large Active Directory (AD) environment. So, I have created a tool called ImproHound to help with that. ImproHound will identifying AD attack paths breaking the AD tier model using the awesomeness of BloodHound. It is available on GitHub including source code, install instructions, and usage guide: https://github.com/improsec/ImproHound
The blogpost explains the motivation for creating ImproHound and what I hope the tool can do for you.
User-mode API hooks and bypasses
TL;DR: security products attempt to monitor process behavior by hooking Win32 APIs in user-mode. However, as the user-mode component of APIs are loaded and owned by the current process, the process itself can inspect, overwrite or simply just not use them and use its own implementation of the API functionality, to avoid messing with the hooks altogether. High-privileged mechanisms such as kernel callbacks should be used instead/in addition.