In this short blog post we will have a quick look at the development of GPU performance since Improsec started four years ago until today.
From the day Improsec started, we’ve used graphics cards (GPUs) to perform password cracking and other crypto attacks for customers, e.g. Active Directory Password Analysis, Penetration Tests, and Red Team engagements.
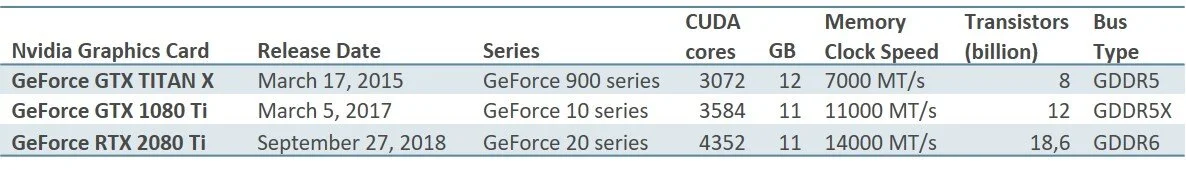
We’ve mainly used three types of GPUs, all from Nvidia. Nvidia cards have served us well with incredible stability, durability and performance. In terms of power consumption they are also very effective, making cooling easier.
Late December 2019 we received a batch of the latest RTX 2080 Ti cards (Founders Edition) from Nvidia, so we thought it could be fun to show the difference in benchmark performance under our favourite password cracking tool, Hashcat.
From a hardware specification perspective, this is what we’re looking at:
The specifications above clearly show, that things have improved over the years, but when putting them to use, the difference becomes obvious and very impressing.
They use about the same power (250-260 Watts pr. card), so in that regards they are comparable. Price-wise they wary a bit, around 6.500 to 9.500 DKK (VAT included), but not a whole lot, and much depends on when you buy (close to launch date it is always the most expensive).
We have used “safe” overclocking where the GPU gets extra power (up to 120%) and fans run with maximum speed, but this had limited effect until the latest cards (as shown below).
Benchmarking this with Hashcat (latest version 5.1.0) and the latest drivers (441.66), taking an average of six runs with the NT-hash algorithm (1000), take a look at how the “Million Hashes per second” numbers increase over time!
We have now more than tripled the cracking speed since the company started (2015), and more than doubled since we bought cards back in 2017.
The sad side of this story is, that password usage is still an essential security risk. Human passwords are not three times better today compared to back when Improsec started (we know because we crack passwords all the time). However, multi-factor authentication and password managers are getting more and more common, so there’s some light ahead :)