This blog post highlights bugs found in installed software during a customer engagement and reported aligned with the Improsec Responsible Disclosure Policy.
Timeline
Improsec identified the vulnerabilities during a customer engagement. Each vulnerability was validated in a simulated Active Directory Lab afterwards.
The vulnerabilities were disclosed to the vendor, IXP Data, on November 11 of 2019.
IXP Data releases EasyInstall version 6.3.101 which patches all six vulnerabilities on November 15 of 2019.
We want to thank IXP Data for an effective and professional response.
CVEs registered (see appendix for more details)
CVE #1: CVE-2019-19897 - Remote Code Execution as SYSTEM via EasyInstall Agent Service
CVE #2: CVE-2019-19896 - Remote Code Execution as SYSTEM via weak permissions on EasyInstall Engine Service share
CVE #3: CVE-2019-19893 - Directory Traversal (TCP 8000) as SYSTEM via EasyInstall Engine Service
CVE #4: CVE-2019-19895 - Lateral Movement using EasyInstall Agent Service against other users on client system
CVE #5: CVE-2019-19894 - Disable UAC using EasyInstall Agent Service on client system
CVE #6: CVE-2019-19898 - Clear-text credentials in network communication (TCP 20050) when using EasyInstall Admininistrator console
What is EasyInstall (IXP)
EasyInstall is a remote management and deployment suite created by IXP Data. A typical setup consists of a EasyInstall Server and various clients each with a EasyInstall agent installed. The agent runs as a service executable on deployed Windows clients.
The affected and tested version is: 6.2.13723
Remote Code Execution as SYSTEM via EasyInstall Agent Service
CVE-ID: CVE-2019-19897
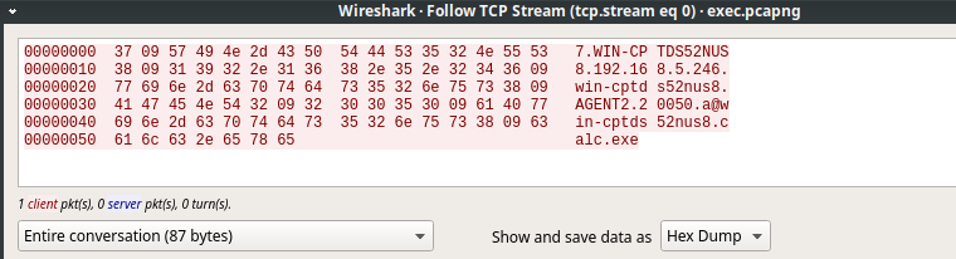
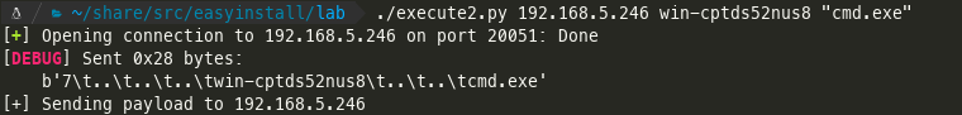
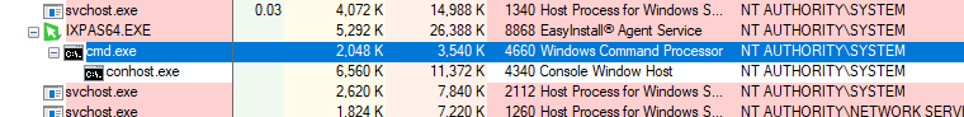
The EasyInstall admin management client features a remote command execution function. This function connects via TCP-port 20051 to the agent on the selected client. By intercepting the TCP-packet with Wireshark we found that the agent performed no authentication or origin check when receiving the TCP-packet
Remote command packet viewed in wireshark
The default packet structure contained various information, however much of the data could be omitted. The required packet structure consists of:
Header bytes(x37x09)
Server name(not needed)
Separator byte(x09)
Server IP(not needed)
Separator byte(x09)
Server name in lowercase(not needed)
Separator byte(x09)
Agent hostname
Separator byte(x09)
Port(not needed)
Separator byte(x09)
Agent version @ server name(not needed)
Separator byte(x09)
Command to execute
A simple python script sending the above packet from any computer on the LAN would gain remote code execution as “NT AUTHORITY” on the client.
Sending packet to client.
cmd.exe executed as “NT AUTHORITY” on the client.
Recommendation
Update to the newest version of EasyInstall.
Remote Code Execution as SYSTEM via weak permissions on EasyInstall Engine Service share
CVE-ID: CVE-2019-19896
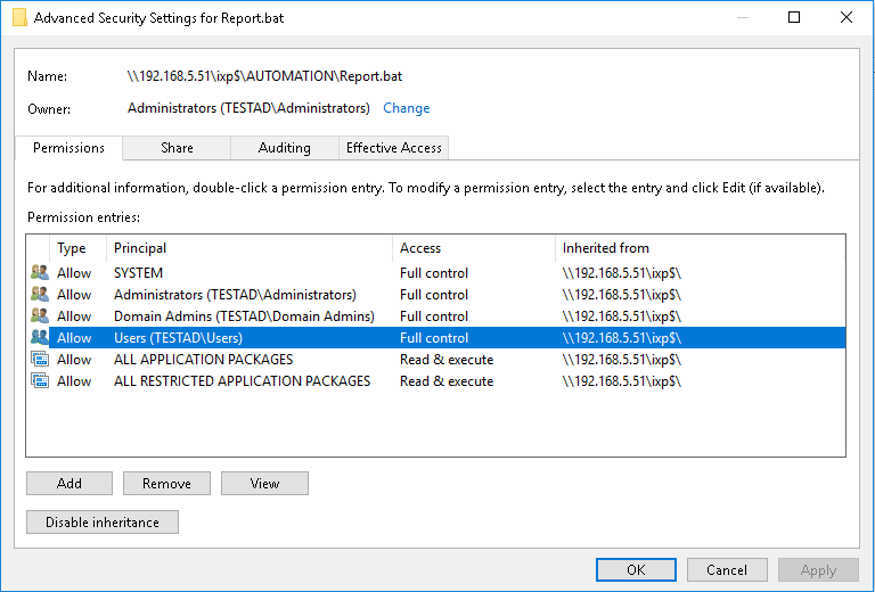
The default EasyInstall installation creates a network share called “IXP$” on the EasyInstall server. Authenticated Active Directory users has read/write rights to this share and some of its sub-directories. This allows for multiple ways to perform remote code execution on the EasyInstall server and its clients as well as privileged escalation on clients.
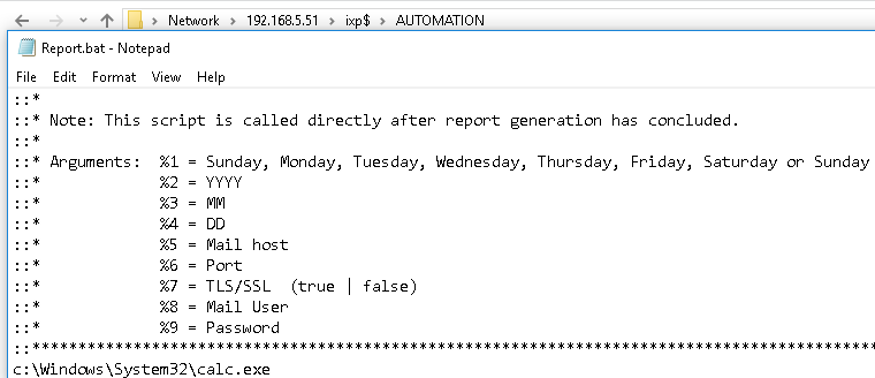
To perform remote code execution on the EasyInstall server, we edited and inserted commands into the BAT-file “Report.bat” in the sub-directory “AUTOMATION”. This file is executed when EasyInstall either automatic or manual creates usage reports. The BAT-file is executed as “NT AUTHORITY/SYSTEM” on the EasyInstall server.
Full access rights to IXP$ share for authenticated users
Adding commands to writable BAT-files on IXP server share
Remote code execution on IXP server
Recommendation
Update to the newest version of EasyInstall.
Directory Traversal (TCP 8000) as SYSTEM via EasyInstall Engine Service
CVE-ID: CVE-2019-19893
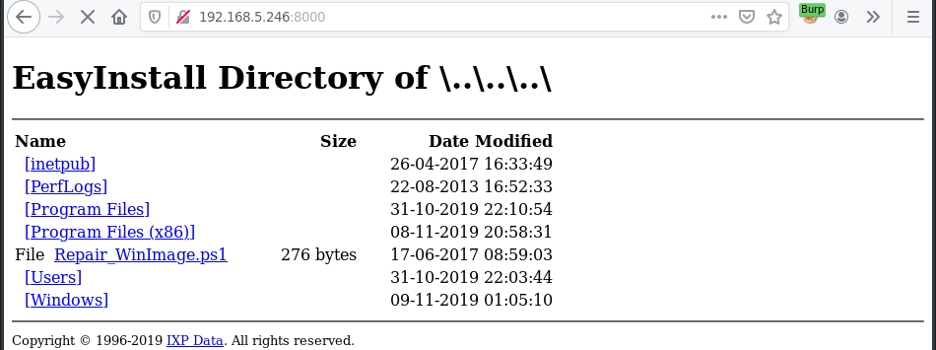
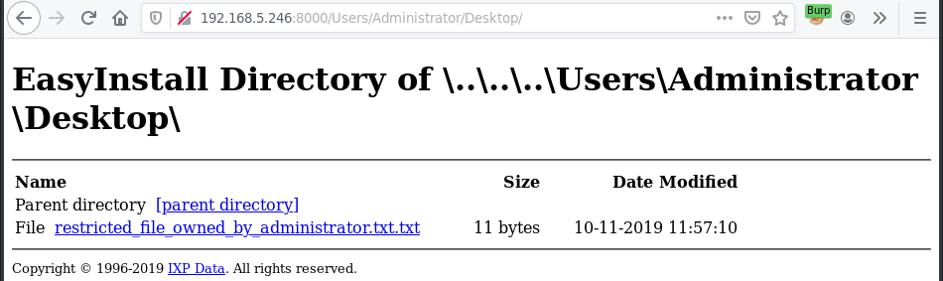
The EasyInstall server deploys by default a custom created web-server on TCP-port 8000. This custom web-server serves the IXP-data directory to any visitors connecting to the web-server. By performing a directory traversal it was possible to access any file on the IXP server in the user context of “NT AUTHORITY”.
Performing directory traversal
Performing directory traversal to directory restricted to local administrator
Recommendation
Update to the newest version of EasyInstall
Lateral Movement using EasyInstall Agent Service against other users on client system
CVE-ID: CVE-2019-19895
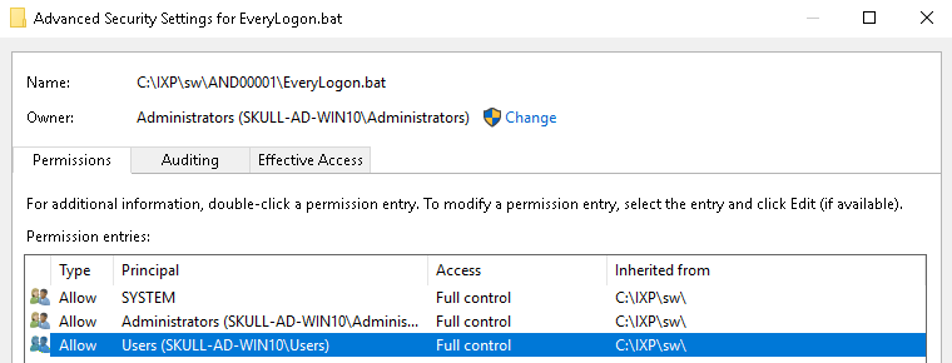
When deploying software packages to a client system the sub-directory “C:” is used as a storage directory for various installation and configuration files. Each software package is placed in a sub-directory with a defined name(fx. AND00001 or SW000231). All authenticated users have read/write rights to these subdirectories and their content. On user logon the EasyInstall agent will traverse each “C:” sub-directory for BAT-files named “EveryLogon.bat” and execute them in the context of the logged on user.
By inserting commands into a “EveryLogon.bat” file, we were able to perform lateral movement on the client system.
File permissions to “EveryLogon.bat”
Inserting commands into BAT-file.
Recommendation
Update to the newest version of EasyInstall
Disable UAC using EasyInstall Agent Service on client system
CVE-ID: CVE-2019-19894
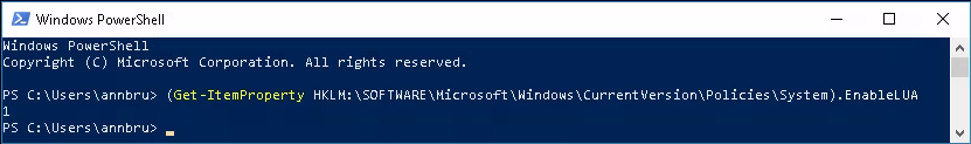
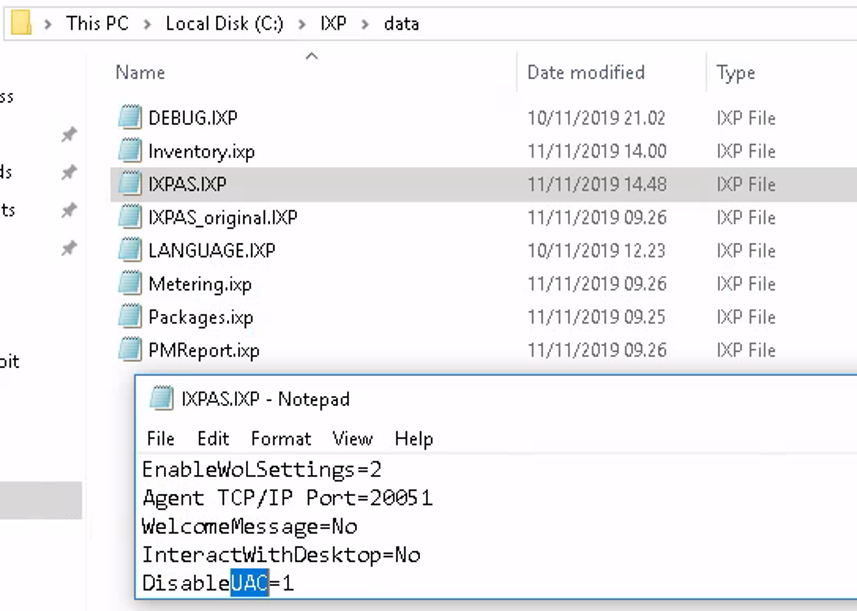
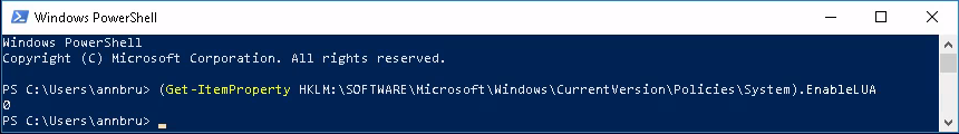
The IXP agent is by default installed to the directory “C:”. This directory is read/write/view restricted by default, however the sub-directory “C:”, which contains the agents configuration files, isn’t restricted for modification of the contained files. This allowed us to create a modified version of the configuration-file “IXPAS.IXP” and rename the original to another filename. The configuration file contained the option: “DisableUAC” which by default enabled UAC. Setting the value to “0” and rebooting the client system disabled UAC for all users. Performing one more reboot restored the default settings.
UAC enabled by default
Disabling UAC via modified “IXPAS.IXP”
UAC disabled after reboot
Recommendation
Update to the newest version of EasyInstall
Clear-text credentials in network communication (TCP 20050) when using EasyInstall Administrator console
CVE-ID: CVE-2019-19898
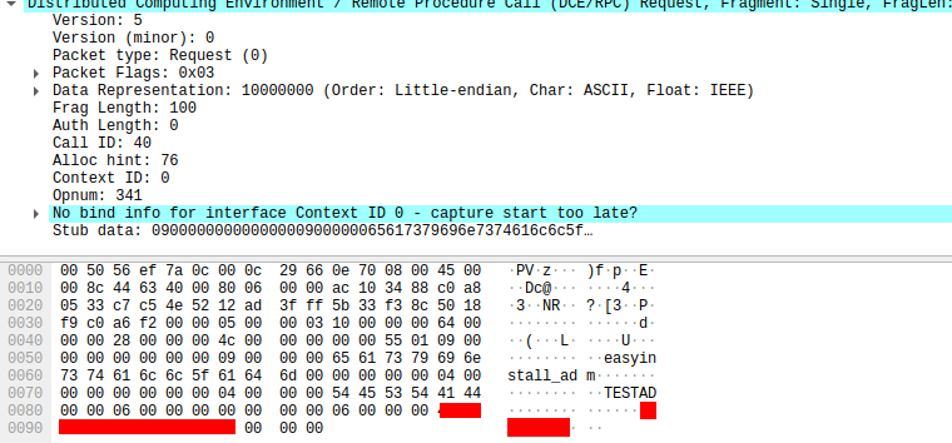
The IXP Administrator application “IXPADM64.EXE” is used by IXP administrators to connect to the deployed IXP server. The application is either used to connect to localhost or a remote server. When using a remote server the administrator username and password is send in clear text to the IXP server instance during login.
Username “easyinstall_adm” and password(hidden with red block) in TCP-packet.
Recommendation
Update to the newest version of EasyInstall
(Updated January 23, fixed CVE IDs and links)