Introduction
Keeping a high security posture on enterprise workstations, is one of the strongest methods to secure and shield your data and intellectual property, against modern attacks.
Attackers strive to gain access to workstations typical through phishing, which then gives them the opportunity to deploy malware. They will then try to escalate their privileges through numerous techniques, such as exploiting an un-patched workstation, which leaves the machine in an unhealthy state, misconfigured services from third party applications, DLL Hijacking and more.
By standardizing and hardening the workstations with a security baseline through policies, configurations, and smart decisions, we can keep the endpoints secure and the attackers at bay.
The intention of this blog post is to describe the minimal required technical configurations that will help to protect against known modern attacks from organized crime, nation state sponsored groups, and other advanced persistent threats. This blog post explains multiple ways to achieve an acceptable security posture, including Group Policies, Hardware Hardening and security software implementation combined with configuration.
By deviating from following recommendations, you will implicitly accept a decrease in your workstation security, thus making it significantly easier for an attacker to compromise it.
Based on knowledge and from what I actually see at our clients, compromising a workstation with its typical “out of box” configuration would be a breeze for any non-sophisticated attacker, and from there it could be a painless journey to escalate their privileges and continue their lateral movement and compromise your entire infrastructure.
Overview
Keeping and maintaining a secure and healthy workstation is a layered approach. Hardening and configuration can, and will, be done in different focus areas, involving:
Boot process
Data Protection
Operating System
Patch Management
Windows Hardening and Group Policies
Unauthorized Code Execution
Endpoint Security
Network Security
Supporting Administrative Practices
Boot Process
Every modern workstation client comes with a feature rich UEFI implementation, which allows to enable or disable settings, which could leave the workstation in an unhealthy and lesser secure state.
By possessing and maintaining a UEFI security baseline shielded and protected with an administrative password, we can ensure that all the necessary UEFI settings are in place, which allows us to leverage from features such as Secure Boot and VBS (Virtualization-based Security).
All unnecessary features and settings in the UEFI should be disabled, and at minimum:
Enforce administrative password upon booting into UEFI or “boot options”
Enable Secure Boot
Enable Intel Virtualization Technology
Enable Modern TPM chip (1.2 or above)
An UEFI baseline could be standardized and deployed with different techniques and models, depending on hardware. If Lenovo is being utilized as hardware, one approach could be a simple PowerShell script, or fancier tools such as Lenovo Think BIOS Config Tool.
Figure 1. Snippet from a Lenovo Think BIOS Config
Data Protection
HDD/SDD Encryption
When users travel, their organization’s confidential data travels with them. Wherever confidential data is stored, it must be protected against unauthorized access. BitLocker provides encryption for full drives, operating system drives and portable drives.
BitLocker Drive Encryption is a data protection feature that integrates with the operating system and addresses the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned computers. BitLocker provides the most protection when used together with a TPM chip version 1.2 or later. The TPM chip works with BitLocker to help protect user data and to ensure that a computer has not been tampered with while the system was offline.
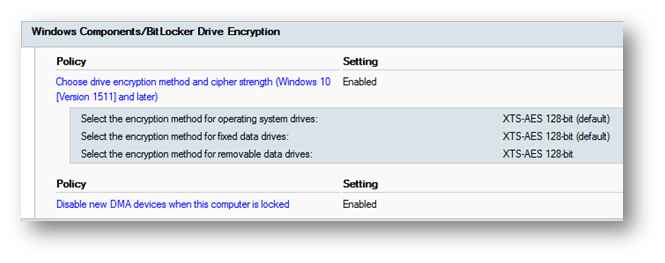
The Operating System disk should be encrypted with BitLocker XTS-AES 128-bit as minimum and should be protected by the Recovery Key stored in the TPM chip and in Active Directory.
Unlocking the BitLocker drive should be done with the TPM chip and a start-up PIN. By utilizing a start-up pin, data on the encrypted volume cannot be accessed without entering the PIN. Using TPM-only validation does not require any interaction with the user to unlock and provide access to the drive. If the TPM validation succeeds, the user sign in experience is the same as a standard logon, which is why implementing BitLocker start-up PIN should be highly considered, when encrypting the workstation drives.
Figure 2. General BitLocker settings from a Group Policy
Figure 3. Operating System Drive BitLocker recommended Group Policy settings
USB device encryption
In addition to fixed data drives encryption, enterprises can leverage from forced BitLocker encryption on portable USB devices through policies. This creates a requirement to encrypt the inserted USB device, before the user can copy and move files from the computer to the USB device, and vice versa.
By forcing BitLocker encryption on USB devices with an unlock-pin, you can protect your data and prevent unauthorized access to the data – even when it is placed on a USB drive.
DMA Protection
Kernel DMA Protection protects PCs against drive-by Direct Memory Access (DMA) attacks using PCI hot plug devices connected to PCI accessible ports, such as Thunderbolt 3 ports.
PCI devices are DMA-capable, which allows them to read and write to system memory at will, without having to engage the system processor in these operations. The DMA capability is what makes PCI devices the highest performing devices available today.
Drive-by DMA attacks are attacks that occur while the owner of the system is not present and usually take less than 10 minutes, with simple to moderate attacking tools (affordable, off-the-shelf hardware and software) that do not require the disassembly of the PC.
A successfully DMA attack could potentially lead to a compromise of the local administrator account, overwriting the password and by then letting the attacker successfully authenticate no matter which password is provided.
Kernel DMA Protection should be enforced, both in the UEFI settings if supported, and in the operating system through policies.
Microsoft’s own Dave Weston demonstrates this attack at Microsoft Ignite here.
Operating System
Windows 10 Enterprise
Windows 10 Enterprise comes shipped with great and must-have security features any organization should leverage from, which is why this is a no-brainer.
A critical security feature which I highly recommend enabling, comes only with Windows 10 Enterprise, and is called Windows Defender Credential Guard.
Some of my recommended configurations also require Windows 10 Enterprise, such as blocking access to the Windows Store, which could potentially put the computer in risk of installing vulnerable software from the store.
Utilizing an EDR (Endpoint Detection and Response) product such as Microsoft Defender for Endpoint also requires Windows 10 Enterprise, which is why it is a must over Windows 10 Pro or Home.
Patch Management
Patch deployment and administration
Patch Management is an important task in maintaining a high security posture. New vulnerabilities are discovered every day and unpatched systems are one of the easier attack vectors for cyber-criminals to take advantage of. Microsoft (and other software vendors) continually release new patches as vulnerabilities are uncovered by researchers and hackers and if your business does not apply these updates then cyber-criminals have an easy entry point into your network.
I recommend that a Patch Deployment procedure with an administrative and managed solution is in place, which allows you to:
Deploy critical patches near instant
Conduct Patch auditing and reporting
Review, improve and repeat
Solutions such as System Center Configuration Manager and Intune (Microsoft Endpoint Manager) is examples of integrated solutions for managing a foundational security baseline on endpoints, and enterprises are typically already paying for the product through their Microsoft 365/EMS licensing.
Figure 4. Windows Update baseline from Microsoft Endpoint Manager
Patch Level of third-party software
Patches can be seen as some type of hotfix. Everyday exploits, bugs, and security risks are identified within programs, and these are what the patches would fix. A bug in the software could be a failure or fault that could cause it to behave in unintended ways.
Keeping third-party software up to date is just as crucial as the underlying operating system itself, which is why using outside vendors and suppliers to support third-party software patching and hotfixes through Microsoft Endpoint Manager is a good choice and makes your IT Administrators life much easier.
Windows Hardening and Group Policies
Policy Security Baselines
By having a baseline and standardization of how policies should affect your workstations, you achieve both a high posture of security but also a complete compliance overview and confirmation, that all workstations are configured correctly, securely and identical. This is an absolute must for configuring a safe workstation.
CIS benchmarks are configuration baselines and best practices for securely configuring a system. Each of the guidance recommendations references one or more CIS controls that were developed to help organizations improve their cyber defence capabilities. CIS controls map to many established standards and regulatory frameworks, including the NIST Cybersecurity Framework (CSF) and NIST SP 800-53, the ISO 27000 series of standards, PCI DSS, HIPAA, and others.
CIS Security Baselines can protect your workstation by enabling various security features, while blocking common entry point attack scenarios.
I recommend enabling and/or disabling features and services, which is and should be included in your Windows 10 Workstation Hardening Baseline:
· Enabling Credential Guard
Uses virtualization-based security to isolate the LSASS process, which can prevent attackers from dumping NTLM hashes.
· Deny workstation to workstation communication by blocking various management ports, including SMB, RPC, WMI, RDP etc.
This could help against and prevent lateral movement and worm-based malware attacks.
· Ensure a strict and tight policy which handles the allowance of logon, both locally and from the network, onto the workstations. This is crucial to prevent lateral movement from potential compromised high-exposure targets.
This includes denying access to the computer from the network from Domain Administrators, Account Operators, Backup Operators, Enterprise Administrators, Schema Administrators etc.
Have a look at my colleagues post on taking this particular problem to the next level with AD Tiering.
· Enforce a high “Default Domain Policy” regarding Password Policy:
Maximum Password History = 24 passwords
Maximum Password Age = 365 days
Minimum Password Age = 1 day
Minimum Password Length = 14 characters
Advanced Password Complexity Requirements = Yes
Local administrator configuration
When denying Domain Administrators access to a workstation, you are left with the only option of using the built-in administrator. Using the built-in administrator (RID 500) the proper way enables you to isolate administrative privileges per workstation, which can help you mitigate the risk of lateral escalation from administrators who have the same local account and password combination on multiple devices.
You should use Microsoft’s own product called LAPS (Local Administrator Password Solution), and no domain or local user should be member of the local administrator group.
To mitigate the risk of an adversary stealing a local administrator account password hash from the local SAM database and abusing it to attack other computers, organizations should ensure every machine has a unique local administrator password. The Local Administrator Password Solution (LAPS) tool can configure unique random passwords on each workstation and store them in Active Directory protected by an ACL. Only eligible authorized users can read or request the local administrator account passwords.
Windows Hello for Business
Administrators can benefit from the ease of use associated with Windows Hello for Business. Administrators can replace their complex passwords with strong two-factor authentication on their PCs. An attacker must have both the device and the biometric info or PIN, which is much more difficult to gain access without the employee's knowledge. Leveraging from Windows Hello for Business could greatly minimize your credential footprint.
Windows Hello for Business can be deployed for both a cloud-only, hybrid or on-premises solution.
Figure 5. WHFB baseline from MEM
Windows Defender Credential Guard
Enabling Credential Guard helps to protect NTLM password hashes, Kerberos Ticket Granting Tickets, and credentials stored by applications as domain credentials. This capability helps to prevent credential theft attacks, such as Pass-the-Hash or Pass-The-Ticket by increasing the difficulty of pivoting in the environment using stolen credentials.
Credential Guard offers better protection against advanced persistent threats when Credential Manager domain credentials, NTLM, and Kerberos derived credentials are protected using virtualization-based security, the credential theft attack techniques and tools used in many targeted attacks are blocked. Malware running in the operating system with administrative privileges cannot extract secrets that are protected by virtualization-based security.
Credential Guard should be enabled and enforced on all Windows 10 devices.
Figure 6. Credential Guard deployed with MEM as a Device Configuration
Windows Defender Exploit Guard
Windows Defender Exploit Guard utilizes the capabilities of the Microsoft Intelligent Security Graph (ISG) to identify active exploits and common behaviours to stop these types of attacks at various stages of the kill chain. The four components of Windows Defender Exploit Guard are designed to lock down the device against a wide variety of attack vectors and block behaviours commonly used in malware attacks, while enabling enterprises to balance their security risk and productivity requirements.
The four components of Windows Defender Exploit Guard are:
· Attack Surface Reduction (ASR)
A set of controls that enterprises can enable to prevent malware from getting on the machine by blocking Office-, script-, and email-based threats
· Network Protection
Protects the endpoint against web-based threats by blocking any outbound process on the device to untrusted hosts/IP through Windows Defender SmartScreen
· Controlled Folder Access
Protects sensitive data from ransomware by blocking untrusted processes from accessing your protected folders
· Exploit Protection
A set of exploit mitigations (replacing EMET) that can be easily configured to protect your system and applications
Windows Defender Exploit Guard should be heavily utilized on all Windows 10 endpoints, with an Attack Surface Reduction Ruleset, as a bare minimum.
Figure 7. ASR Rules deployed with Group Policies
Unauthorized Code Execution
Application Control
Application control can help mitigate numerous types of security threats by restricting the applications that users are allowed to run and the code that runs in the System Core (kernel). Application control policies can also block unsigned scripts and MSIs, and restrict Windows PowerShell to run in Constrained Language Mode.
I highly recommend utilizing Microsoft’s own WDAC (Windows Defender Application Control) or AppLocker, depending on the organization and the purpose of the hardening objective. AppLocker will be deployed through Group Policy, and WDAC can be deployed through Group Policies, MEM Configurations and PowerShell scripts.
Although either AppLocker or WDAC can be used to control application execution on Windows 10 clients, the following factors can help you decide when to use each of the technologies.
WDAC is best when:
You are adopting application control primarily for security reasons.
Your application control policy can be applied to all users on the managed computers.
All of the devices you wish to manage are running Windows 10.
AppLocker is best when:
You have a mixed Windows operating system (OS) environment and need to apply the same policy controls to Windows 10 and earlier versions of the OS.
You need to apply different policies for different users or groups on a shared computer.
You are using application control to help users avoid running unapproved software, but you do not require a solution designed as a security feature.
You do not wish to enforce application control on application files such as DLLs or drivers.
You should definitely check out my colleague’s blog post, which covers exactly what I am preaching.
Microsoft just dropped a tool called “WDAC Policy Wizard” which makes creating and deploying WDAC a breeze. I strongly urge you to utilize this tool, to keep your sanity in check.
PowerShell configuration
Given that PowerShell cannot and should not be disabled or removed from organizations that require it, the following actions are the recommended best practices to use PowerShell efficiently while preventing its use as an attack vector.
PowerShell Constrained Language Mode
Constrained language mode is a way of restricting access to sensitive language elements that can be used to invoke arbitrary Windows APIs. It was designed to work with system-wide application control solutions such as Device Guard User Mode Integrity (UMCI).
Figure 8. Constrained Language Mode blocking importing modules
PowerShell with AppLocker and Windows Defender Application Control
Before a script file is run, PowerShell invokes AppLocker to verify the script. AppLocker invokes the Application Identity component in user-mode with the file name or file handle to calculate the file properties. The script file is then evaluated against the AppLocker policy to verify that it is allowed to run.
With WDAC we are able not only to control applications, but also to control whether specific plug-ins, add-ins, and modules can run from specific apps.
Disabling PowerShell V.2
PowerShell V.2 has been deprecated since August 2017, but it is still available by default on the Windows 10 operating system. PowerShell V.2 is like candy for attackers since it does not support Constrained Language Mode, AMSI Protection and richer logging features like its successor PowerShell v.5.
Figure 9. Constrained Language Mode being bypassed by using PowerShell v.2
Endpoint Security
Antivirus (AV) & EDR (Endpoint Detection and Response)
EDR security provides organizations with the means to monitor, detect, and respond to endpoint threats. Through the application of EDR solutions and practices, organizations gain visibility into the endpoint of the network. EDR also provides organizations with the tools to protect the network against incoming threats as they occur.
EDR is the sub-field of endpoint security responsible for proactively defending the network against endpoint threats. EDR security is composed of practices and technologies that actively monitor endpoint activity, identify threats, and trigger automatic responses to attacks.
EDR also gives greater insight into what happened on a workstation and how an attacker behaved once an initial foothold had been gained.
You should not ignore a good AV product, and actually Windows 10 comes shipped with an excellent AV software called Windows Defender, which you unquestionably should tune and optimize with Group Policies or Device Configuration Policies from Microsoft Endpoint Manager . Windows Defender Antivirus can be combined with Windows Defender for Endpoint to create a complete Antivirus & EDR solution.
There is not much more to say about AV other than do it - and do it right! And if you are serious about your enterprise and workstation security, I urge you to invest in an EDR product, and combine it with your AV.
Microsoft Defender Antivirus with “Cloud Protection” enabled combined with Microsoft Defender for Endpoint, is a great example of 2 different products (AV & EDR) working firmly in sync, to establish a layered approach to your workstation security.
Figure 10. Microsoft Defender for Endpoint Dashboard
Network Security
Support of legacy/insecure protocols
Still to this day, Microsoft ships Windows 10 with several enabled old and legacy insecure protocols. Attackers like to abuse these types of protocols, since they usually lack effective protections to prevent unauthorized tampering. Most of the protocols are either not used or has been replaced by their successor.
Following insecure and legacy protocols should be disabled:
NetBIOS
LLMNR
WPAD
SMB1
Firewall configuration
By utilizing and leveraging from the Windows Defender Firewall with Advanced Security, we can restrict various incoming communication to the workstation, which greatly reduces the attack surface for the Windows 10 client.
You should look into implementing the following Windows Defender Firewall with Advanced Security rules:
· Firewall state set to = On
Domain, Private, Public
· Inbound connections set to = Block (default)
Blocks incoming connections unless they are stated in a rule
· Outbound connections set to = Allow (default)
Allow all outbound communication from the Windows 10 client
· Block incoming connections
Incoming Rules
Port 80 (http)
Port 443 (https)
Port 135 (RPC)
Port 137-139 (NetBIOS)
Port 445 (SMB)
Port 3389 (RDP)
Port 5985 (WinRM & wsman - http)
Port 5986 (WinRM & wsmans – https)
Supporting Administrative Practices
Remote Support of users
RDP (Remote Desktop Protocol) is the native way of utilizing remote access to and from a workstation or server, and that is why it is a common target on various attacks on Windows 10 clients.
Since I recommend blocking incoming RDP connections to the Windows 10 device through the Windows Defender Host Firewall, this leaves a gap in the possibility of remote access availability for the administrator.
Should the organization find it necessary to leverage from RDP, it is crucial to secure the authentication and integrity of the RDP session, to ensure security best practices such as:
· 2FA (2-factor authentication)
Could be achieved with combining Azure MFA and a Remote Desktop Gateway server with the Network Policy Server (NPS) extension
Virtual Smart Card using TPM provisioned with a sign-in certificate, provided with a PIN
· IPSec
Check out my other colleague’s blog post describing the functionality and implementation of IPSec.
· Windows Defender Remote Credential Guard
Blocks NTLM authentication (allowing only Kerberos) which prevents Pass-the-hash (PtH) attacks, and is the successor to Restricted Admin Mode
Final word
Let’s face it. If an Advanced Persistent Threat (APT) or Nation State Sponsored hacker group desperately wants to compromise your enterprise workstation, they will get the job done – but that doesn’t mean we should make it easy for them.
If you have implemented the covered best practices and features in this post, you made it extremely hard for an attacker to gain a foothold into your network, and if they actually got it, you will give them a headache trying to move laterally in order to scout and compromise potential high value targets, such as Domain Controllers or Federation Services servers.